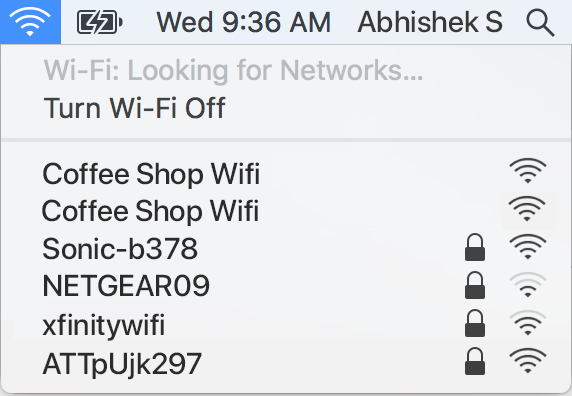
Client-side rogue access-point detection using a simple walking strategy and round-trip time analysis | EURASIP Journal on Wireless Communications and Networking | Full Text

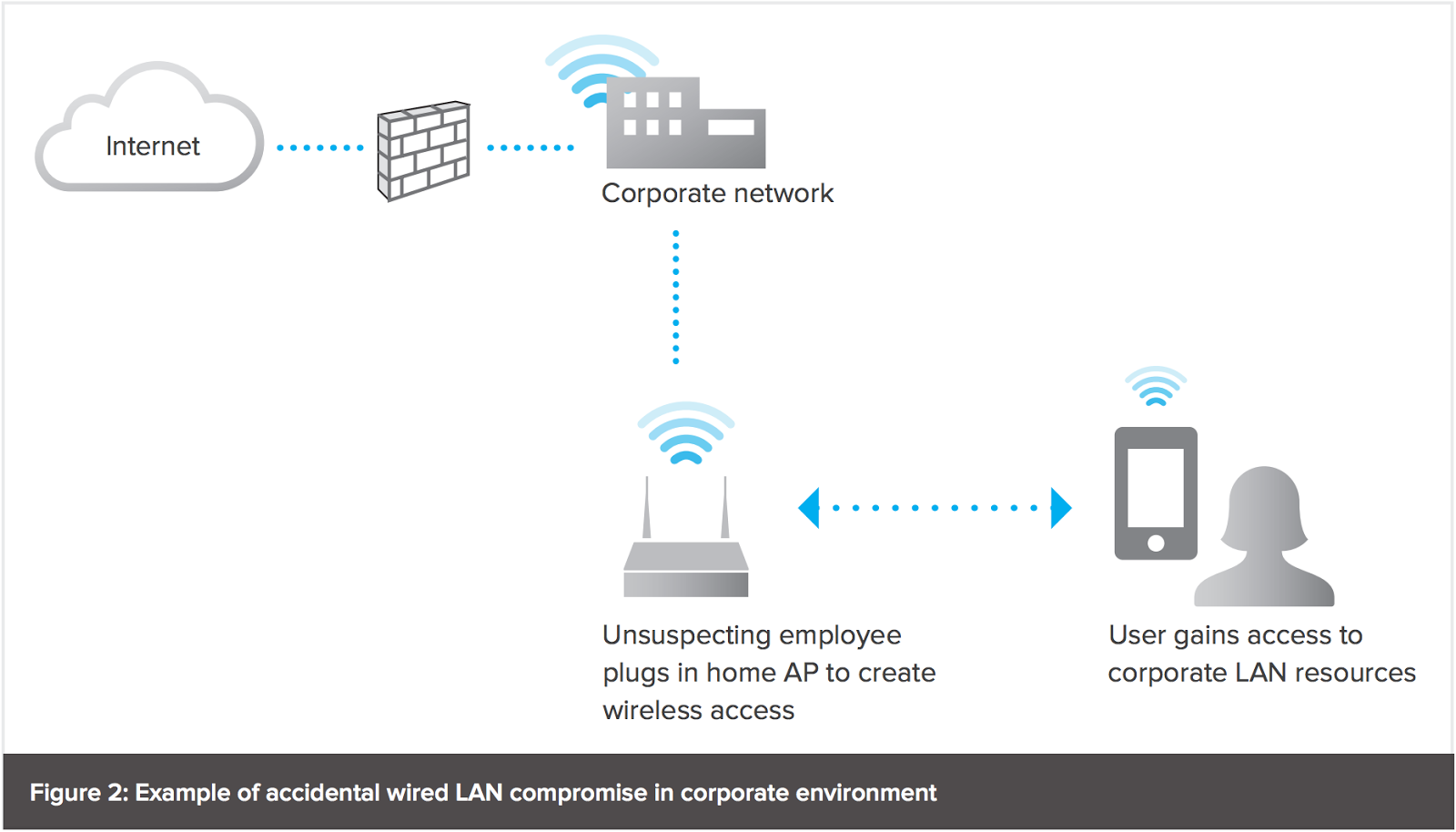
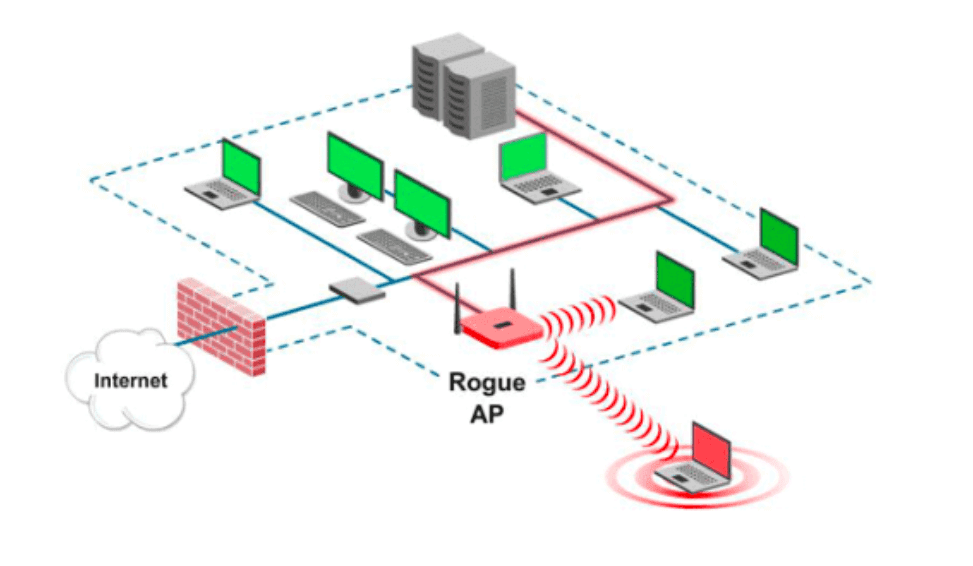
This figure shows the setup of a rogue AP. A rogue AP is connected to... | Download Scientific Diagram

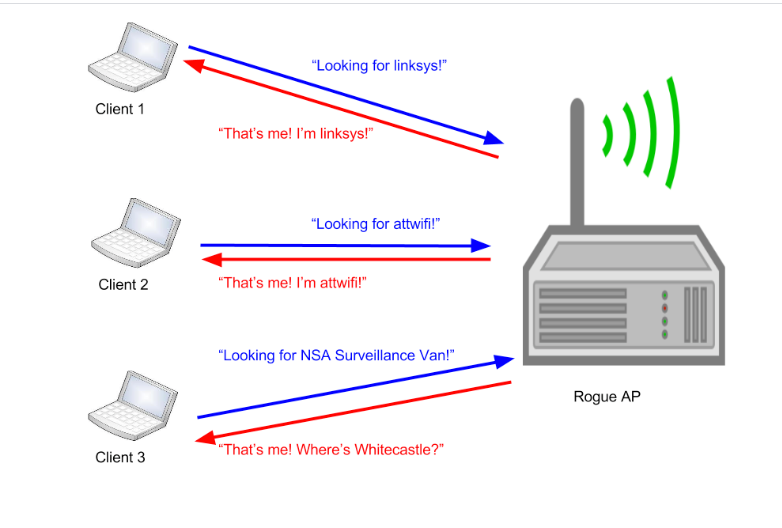
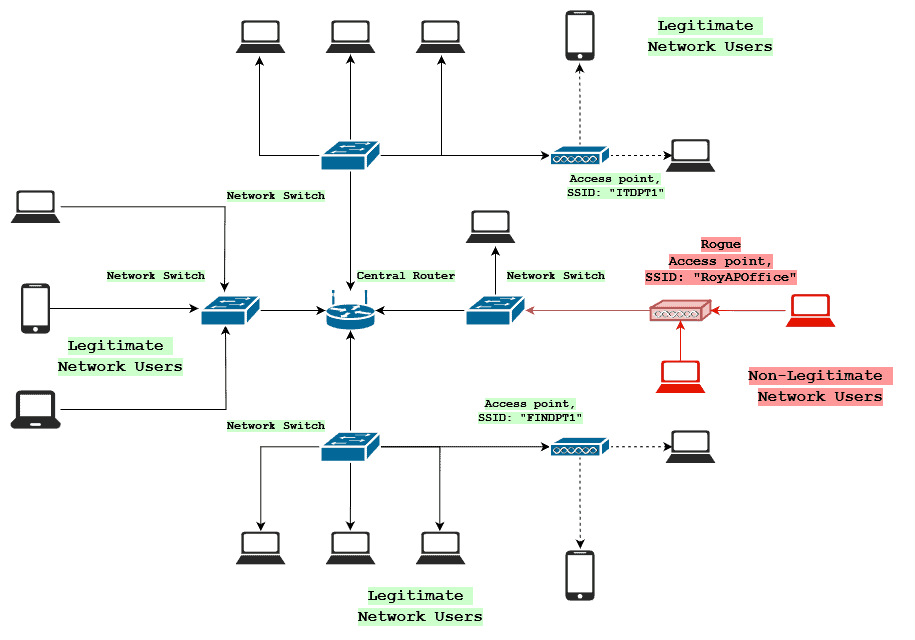
Rogue Access Points and Evil Twins - CompTIA Security+ SY0-501 - 1.2 - Professor Messer IT Certification Training Courses


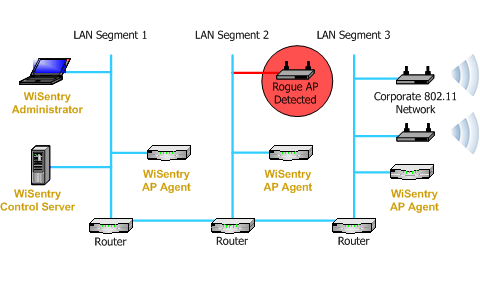



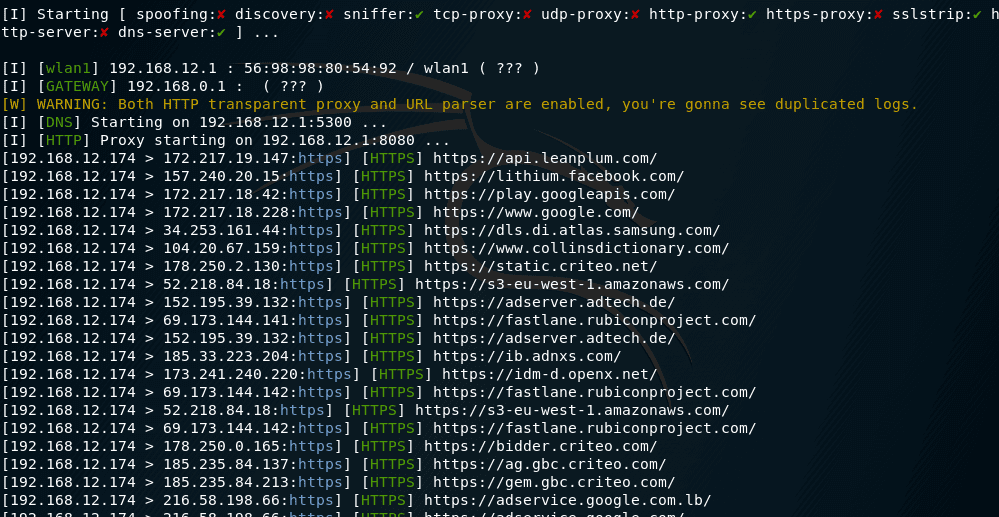


![PDF] A Flexible Framework for Rogue Access Point Detection | Semantic Scholar PDF] A Flexible Framework for Rogue Access Point Detection | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5f7a2fec5198aa5b1f3c846b4db50aec4dff4e3b/29-Figure2.2-1.png)