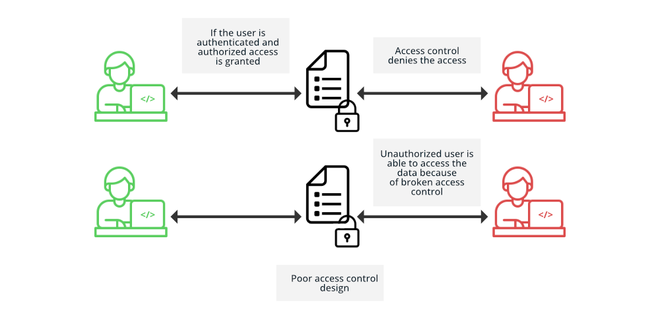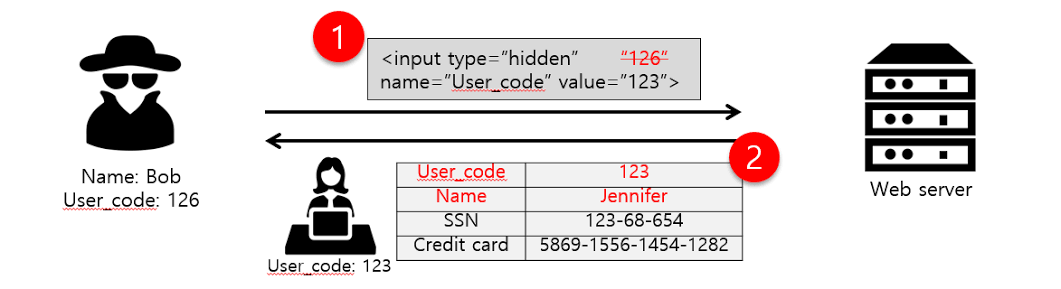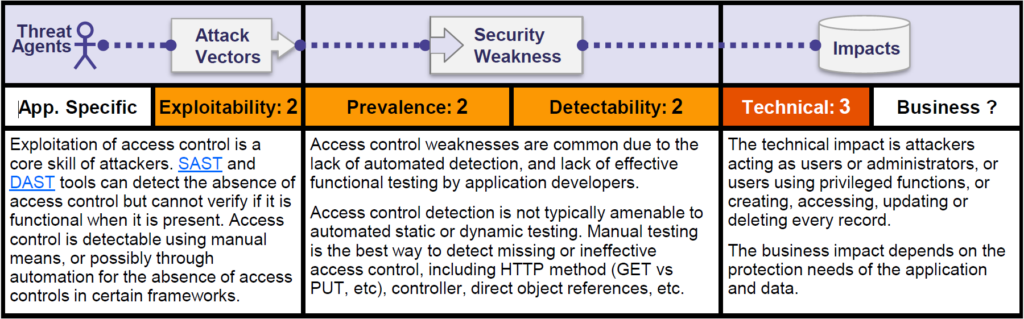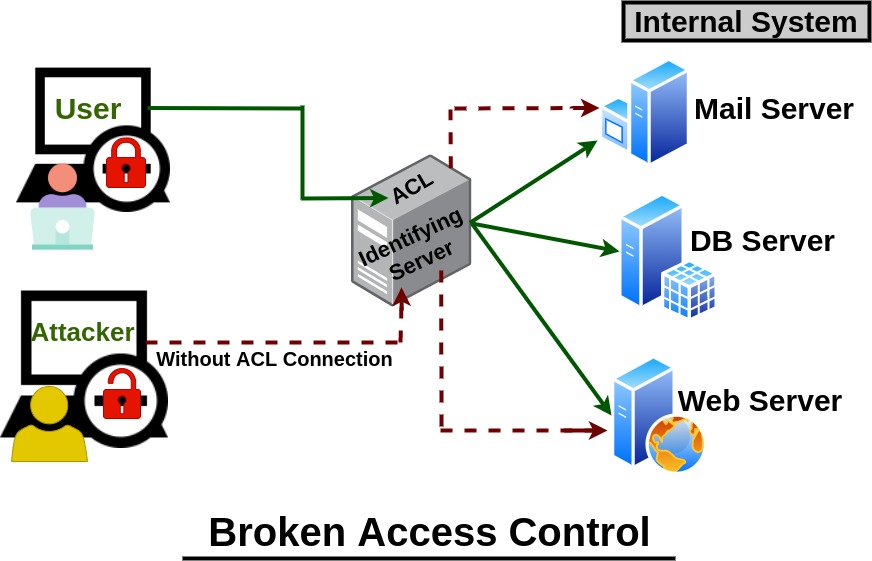
Comprehension The Risk of "Broken Authentication & Broken Access Control" - The most popular web application threats - Cloudkul

Malaysia IT Professional Network - Broken Access Control is listed under OWASP Top 10, thus the need for web security is real. To gain more on the best practices to combat incoming

How to Catch the Top OWASP 2021 Security Category - Broken Access Control - in Code Review | PullRequest Blog