Data Integrity: Exploring Message Authentication Codes and Digital Signatures - EngineerZone Spotlight - EZ Blogs - EngineerZone

HMAC Construction HMAC uses the following parameters: H = hash function... | Download Scientific Diagram

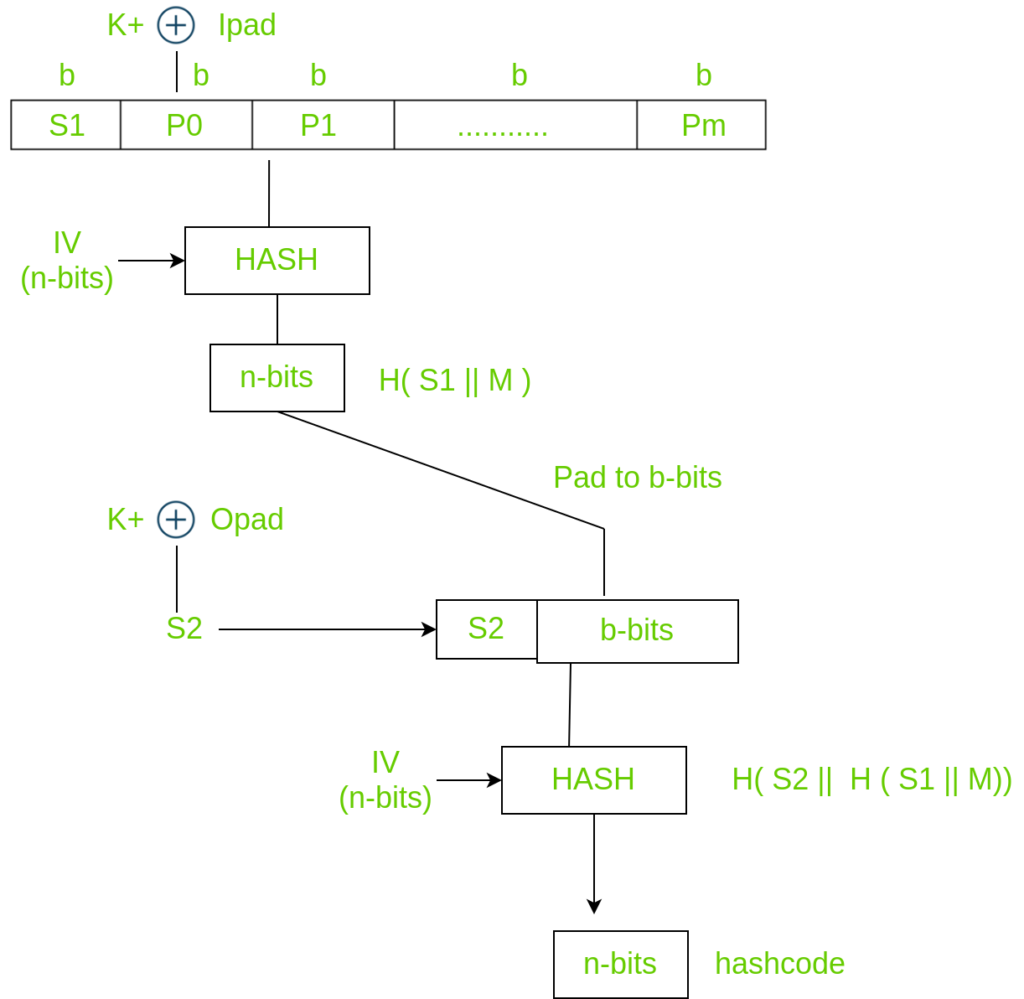
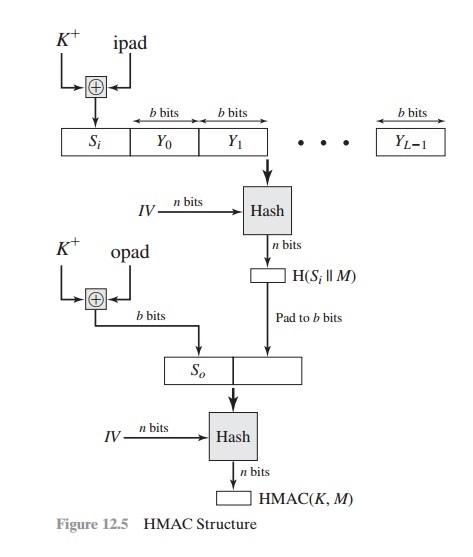
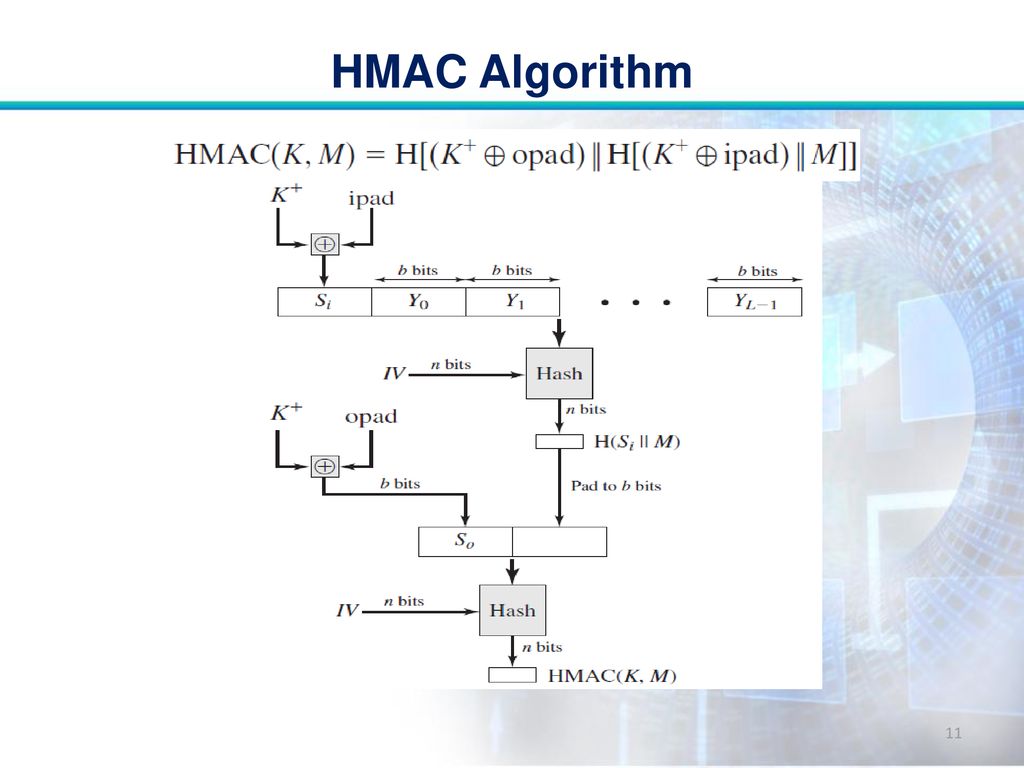
SOLVED: Please explain this picture. K+ iPad b bits b bits Y1 b bits YL-1 Si Yo HMAC n bits IV Hash opad bits HSIM K Structure b bits pad to b

Hash Message Authentication Code (HMAC) process. 3.3.2. Overview of... | Download Scientific Diagram

Chirag's Blog: HMAC | MAC based on Hash Function | HMAC Structure | HMAC Impelmentation | HMAC Pros & Cons
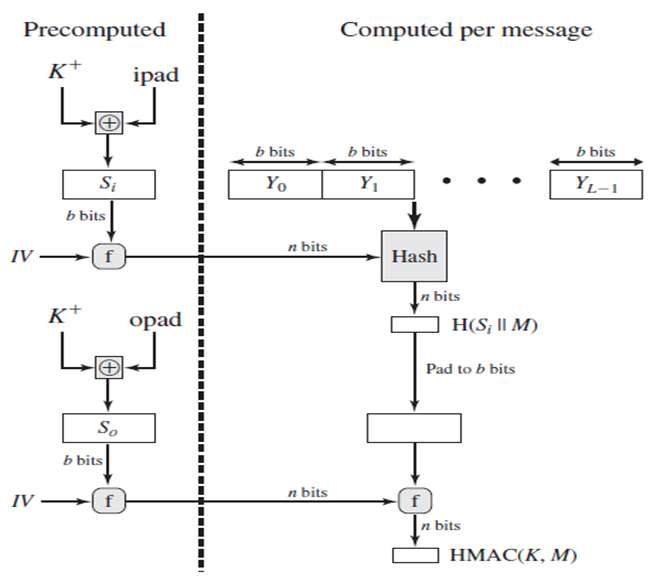
Chirag's Blog: HMAC | MAC based on Hash Function | HMAC Structure | HMAC Impelmentation | HMAC Pros & Cons

HMAC - Lecture materials - HMAC Hash-based Message Authentication Code Developed by Mihir - Studocu
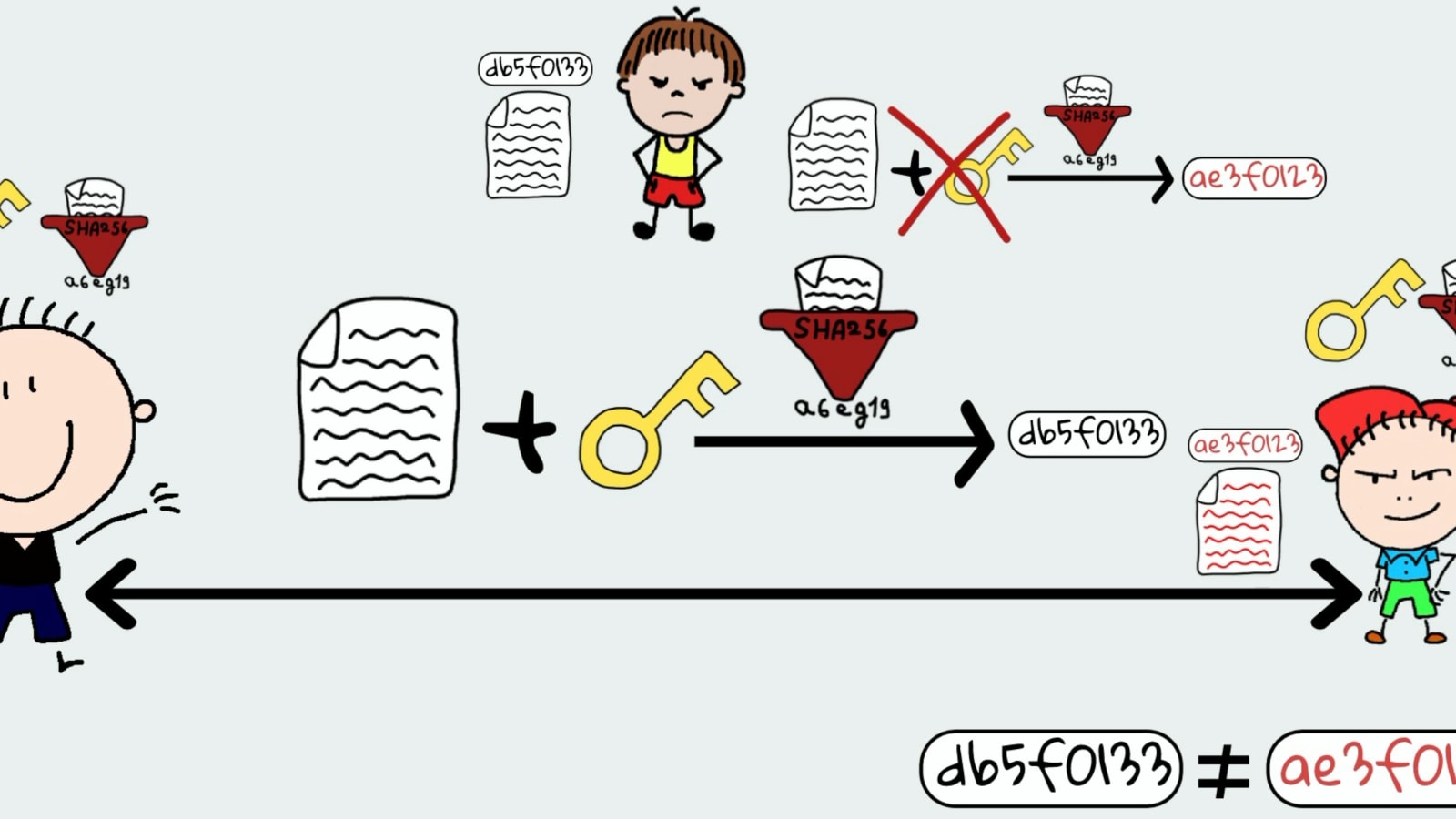







![암호학] HMAC(Hashed MAC) 개념과 과정 암호학] HMAC(Hashed MAC) 개념과 과정](https://blog.kakaocdn.net/dn/1s1Vf/btqEh6BOJV3/Bwk3afhbGhcz4yFKTlWeA0/img.png)