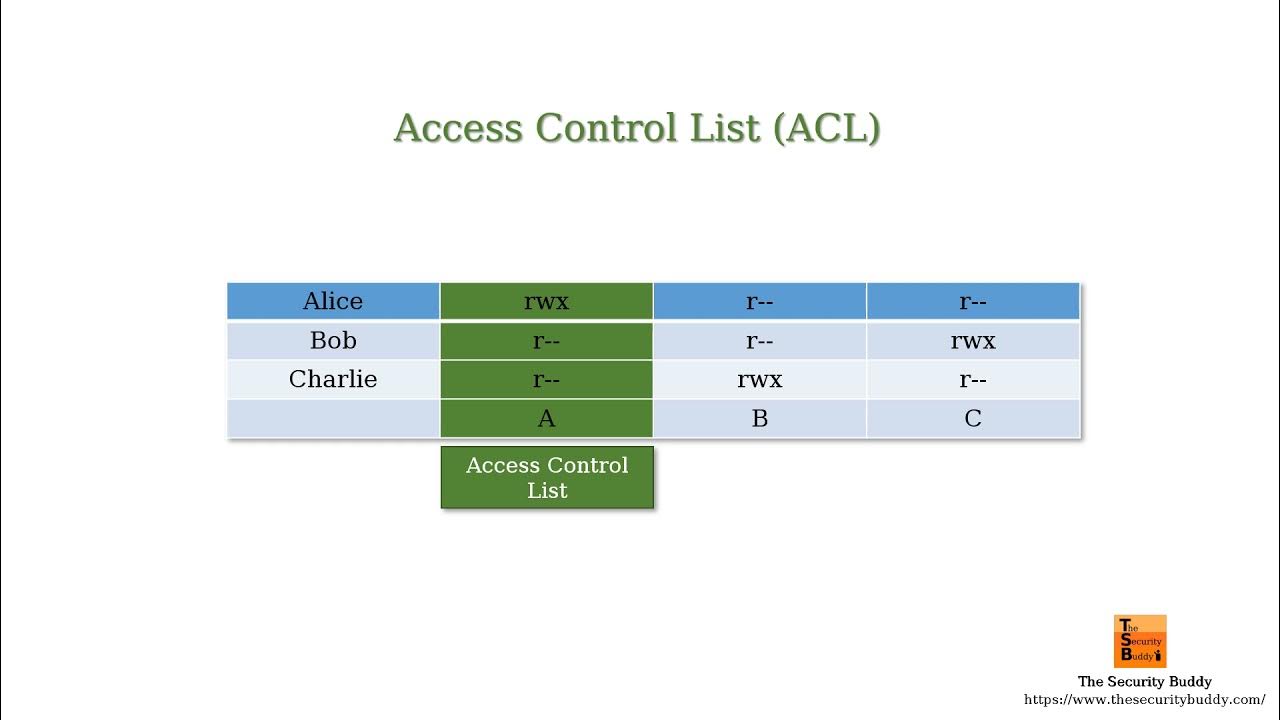
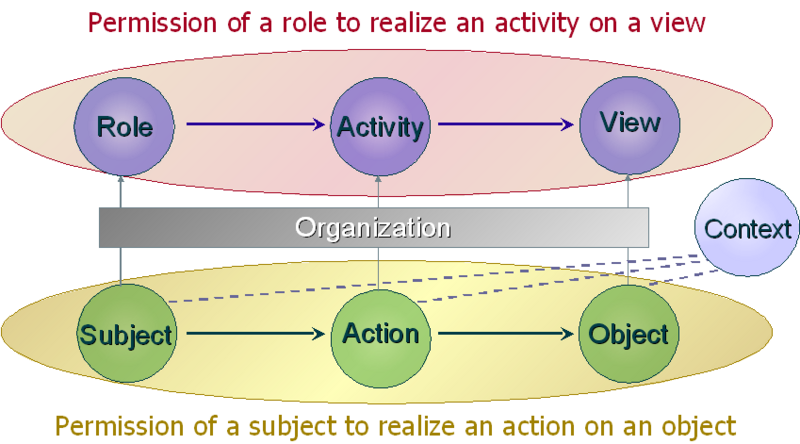
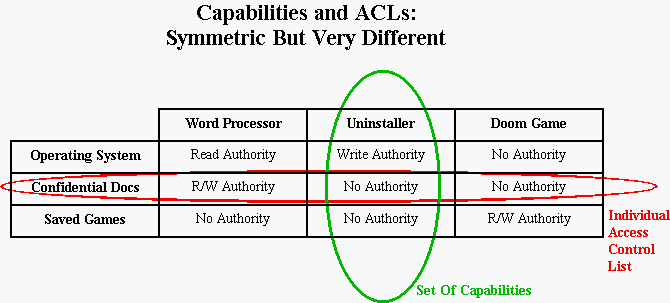
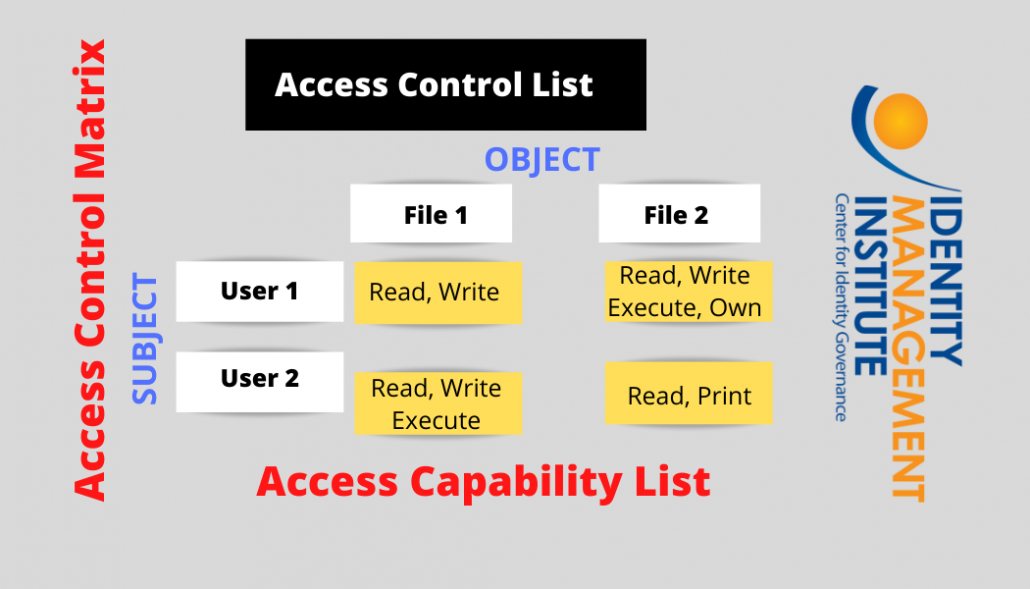
Capability-based security — enabling secure access control in the decentralized cloud | by Kevin Leffew | Medium

Capability-Based Access Control with ECC Key Management for the M2M Local Cloud Platform | SpringerLink

provides examples of potential usage of capability based authorization... | Download Scientific Diagram

A capability-based security approach to manage access control in the Internet of Things - ScienceDirect

A capability-based security approach to manage access control in the Internet of Things | Semantic Scholar

A capability-based security approach to manage access control in the Internet of Things - ScienceDirect

Capability-Based Access Control with ECC Key Management for the M2M Local Cloud Platform | SpringerLink
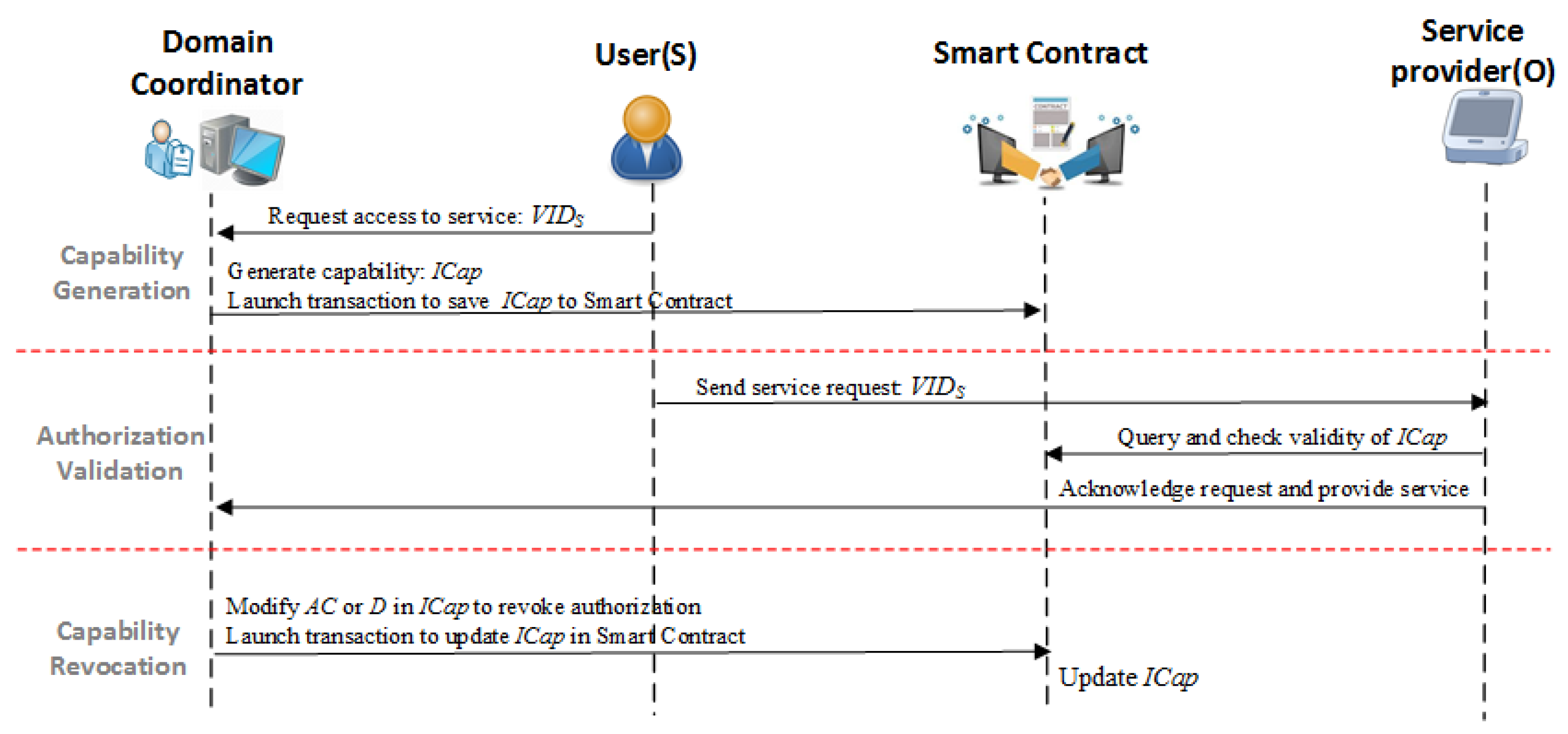

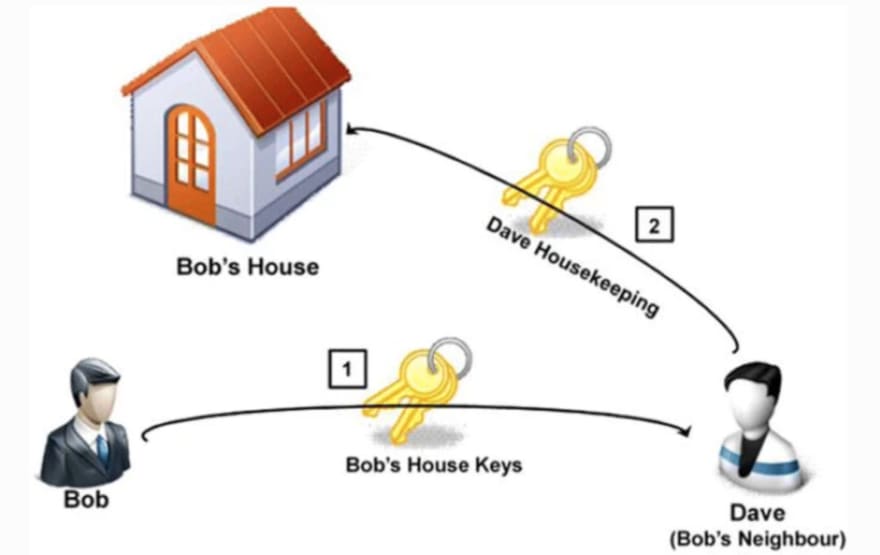

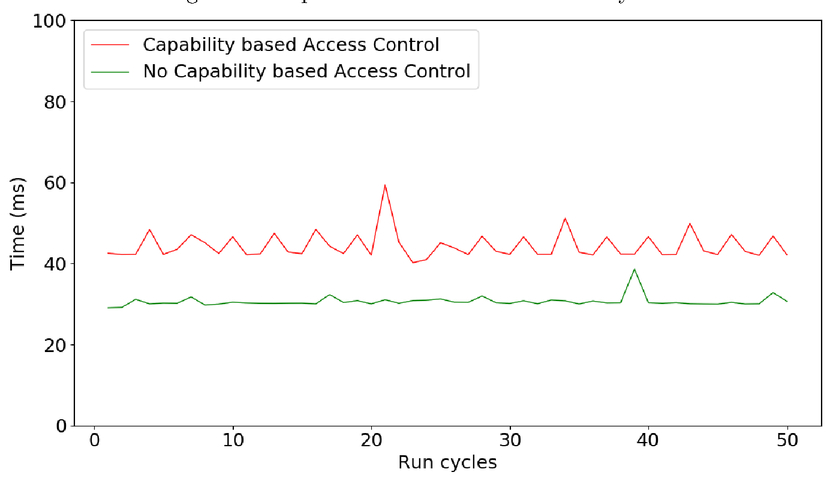

![PDF] Distributed Capability-based Access Control for the Internet of Things | Semantic Scholar PDF] Distributed Capability-based Access Control for the Internet of Things | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/972fd21ba4a8049d43e370305ae0e2fc3b378e55/5-Figure2-1.png)