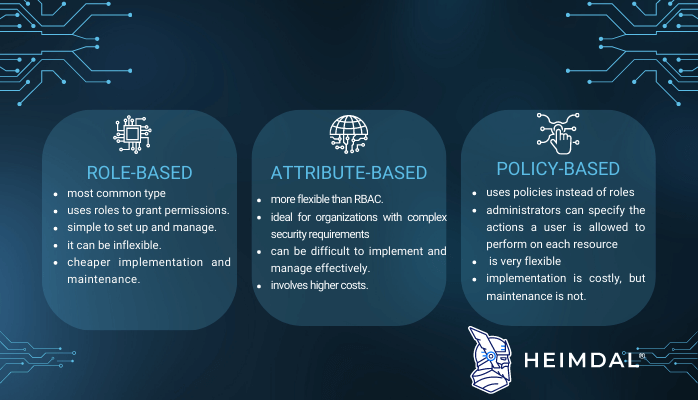
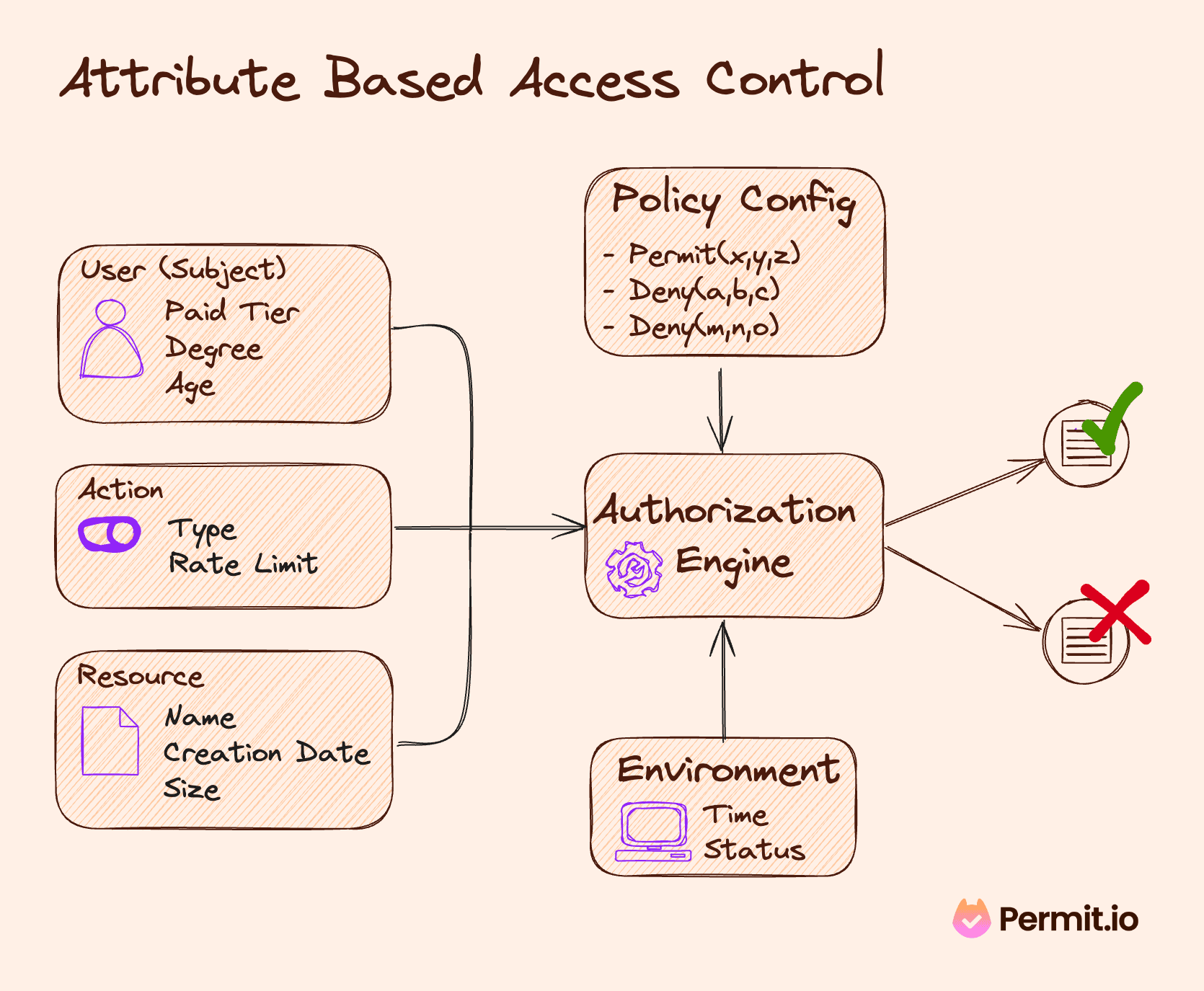
Research Summary: Efficient Attribute-Based Smart Contract Access Control Enhanced by Reputation Assessment - Auditing and Security - Smart Contract Research Forum
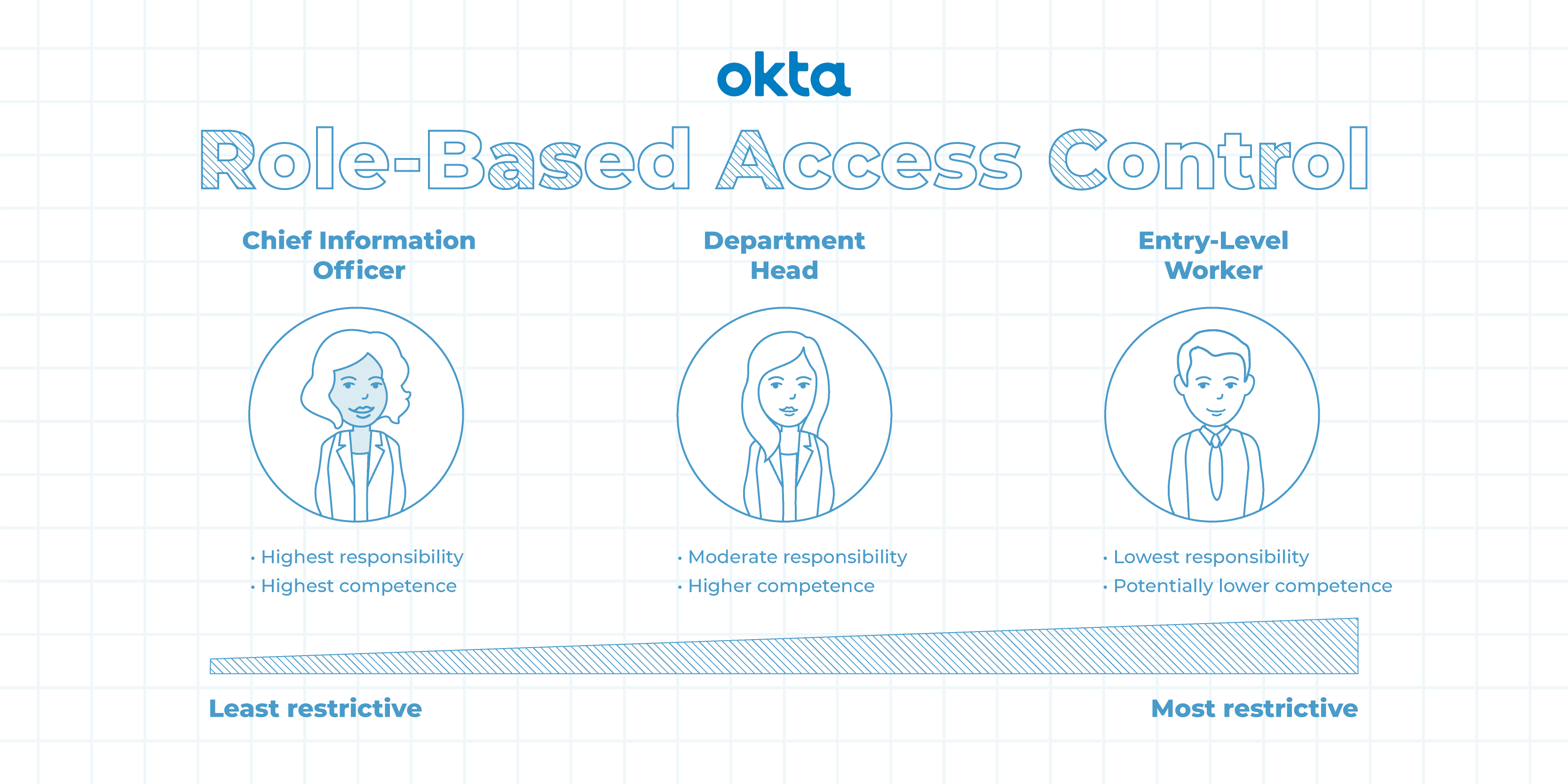
Attribute-based Access Control (ABAC) and a DDD application - Questions / Help - Elixir Programming Language Forum

Figure 4 from Guide to Attribute Based Access Control (ABAC) Definition and Considerations | Semantic Scholar
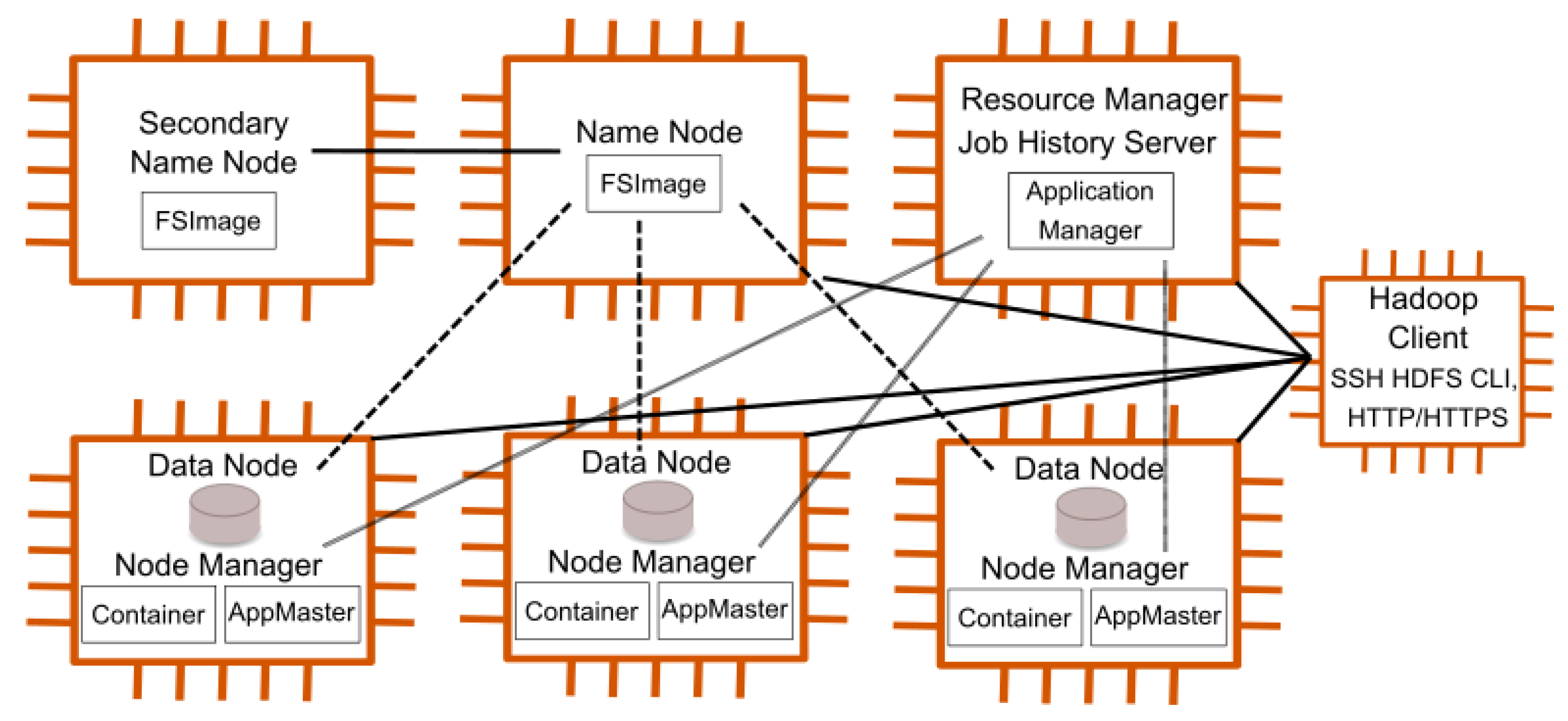
Applied Sciences | Free Full-Text | A Framework for Attribute-Based Access Control in Processing Big Data with Multiple Sensitivities
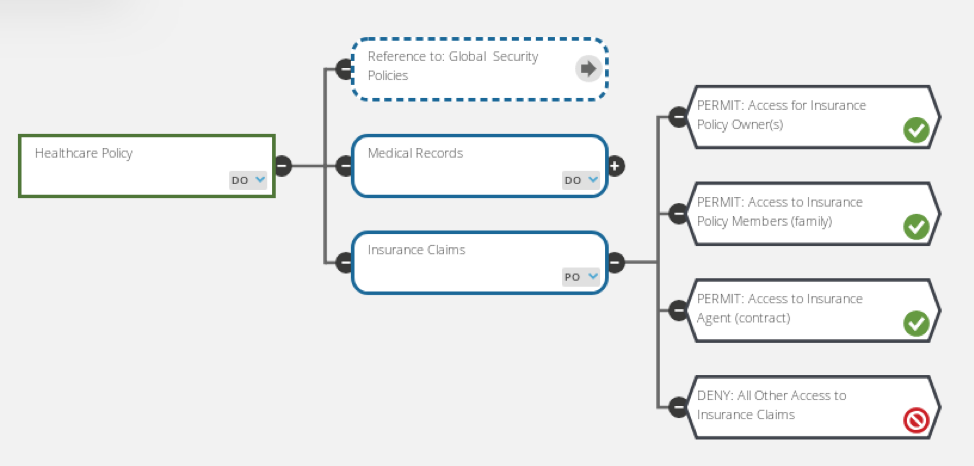

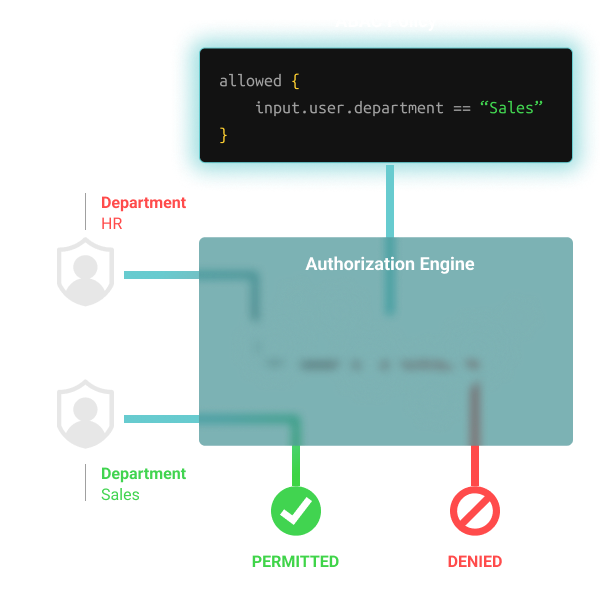
![PDF] Attribute-Based Access Control | Semantic Scholar PDF] Attribute-Based Access Control | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f2d698c5a1819b0cff0c8899b8a391c5721aa2b6/2-Figure1-1.png)