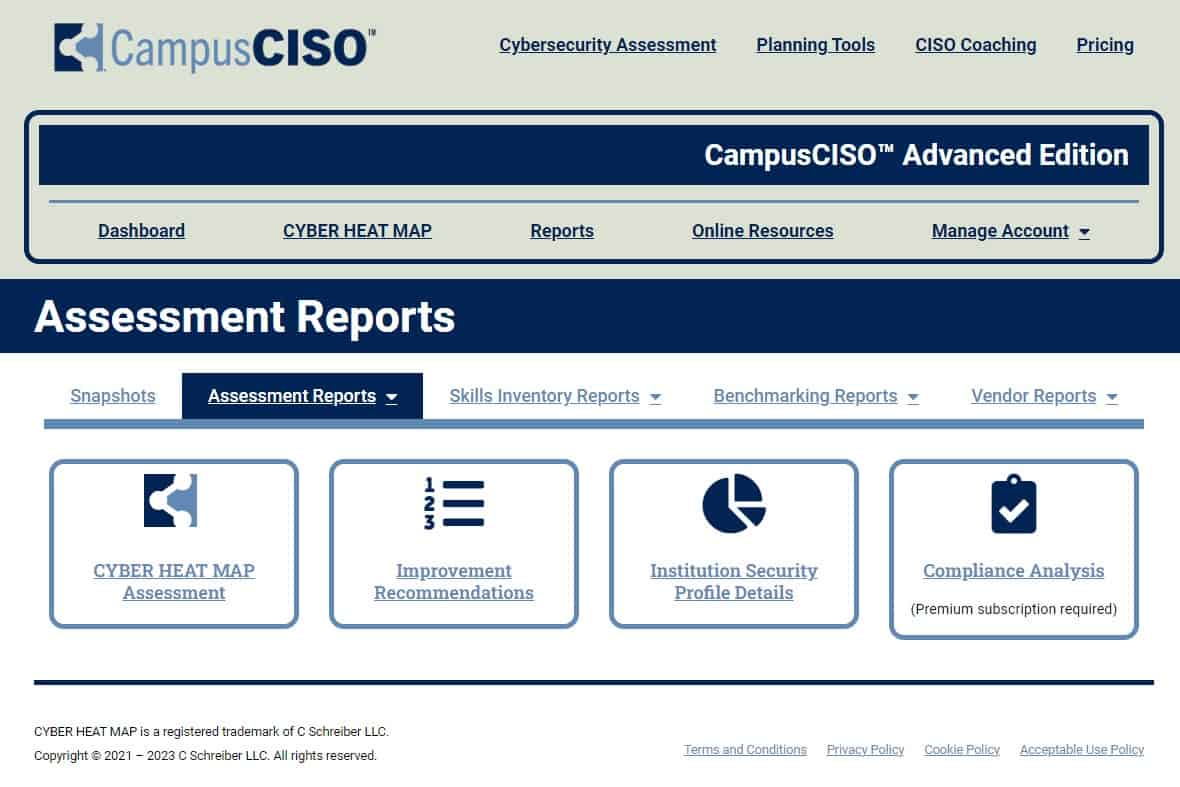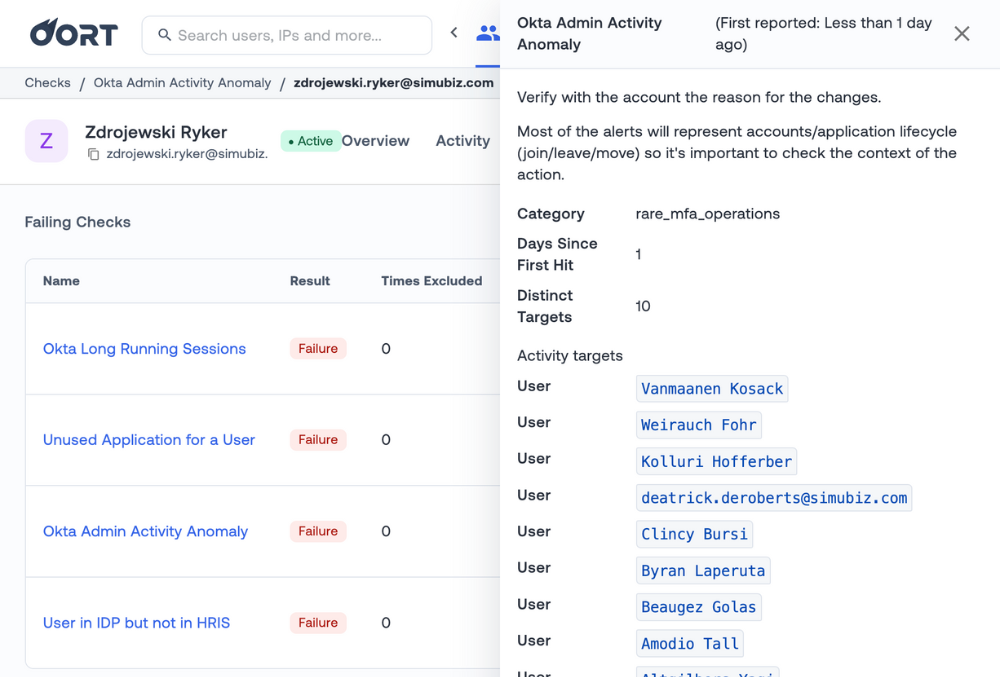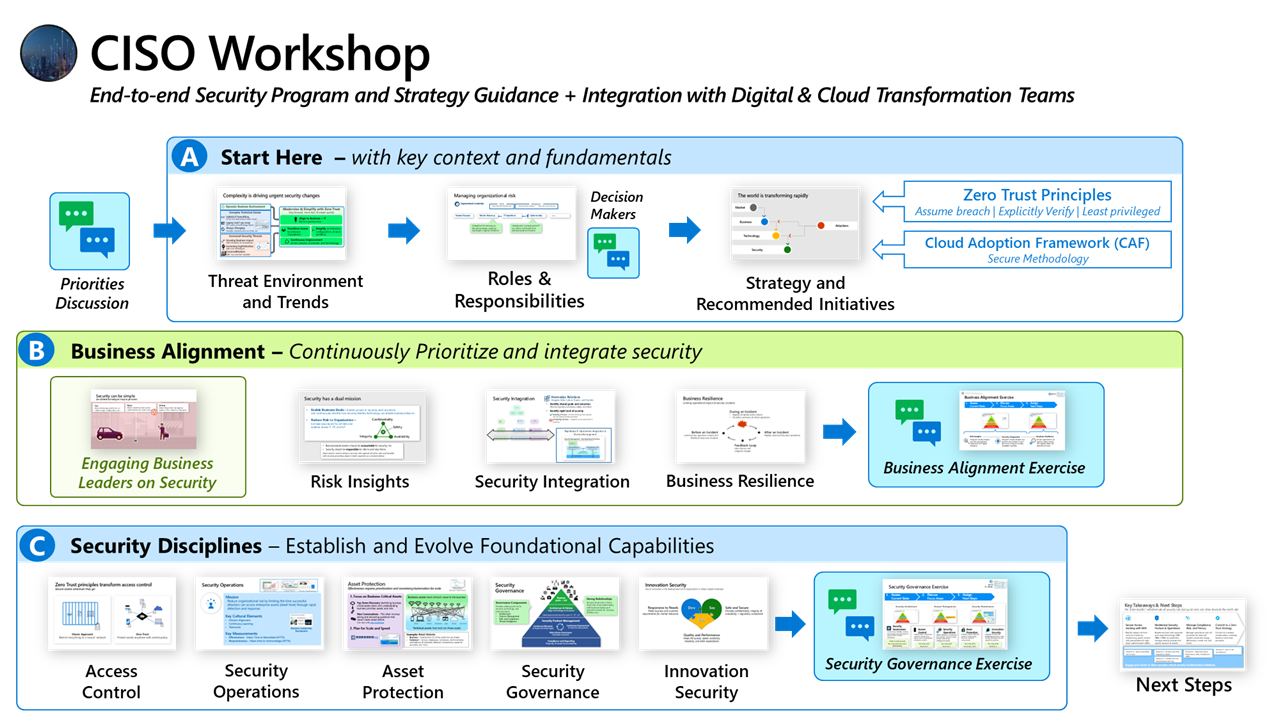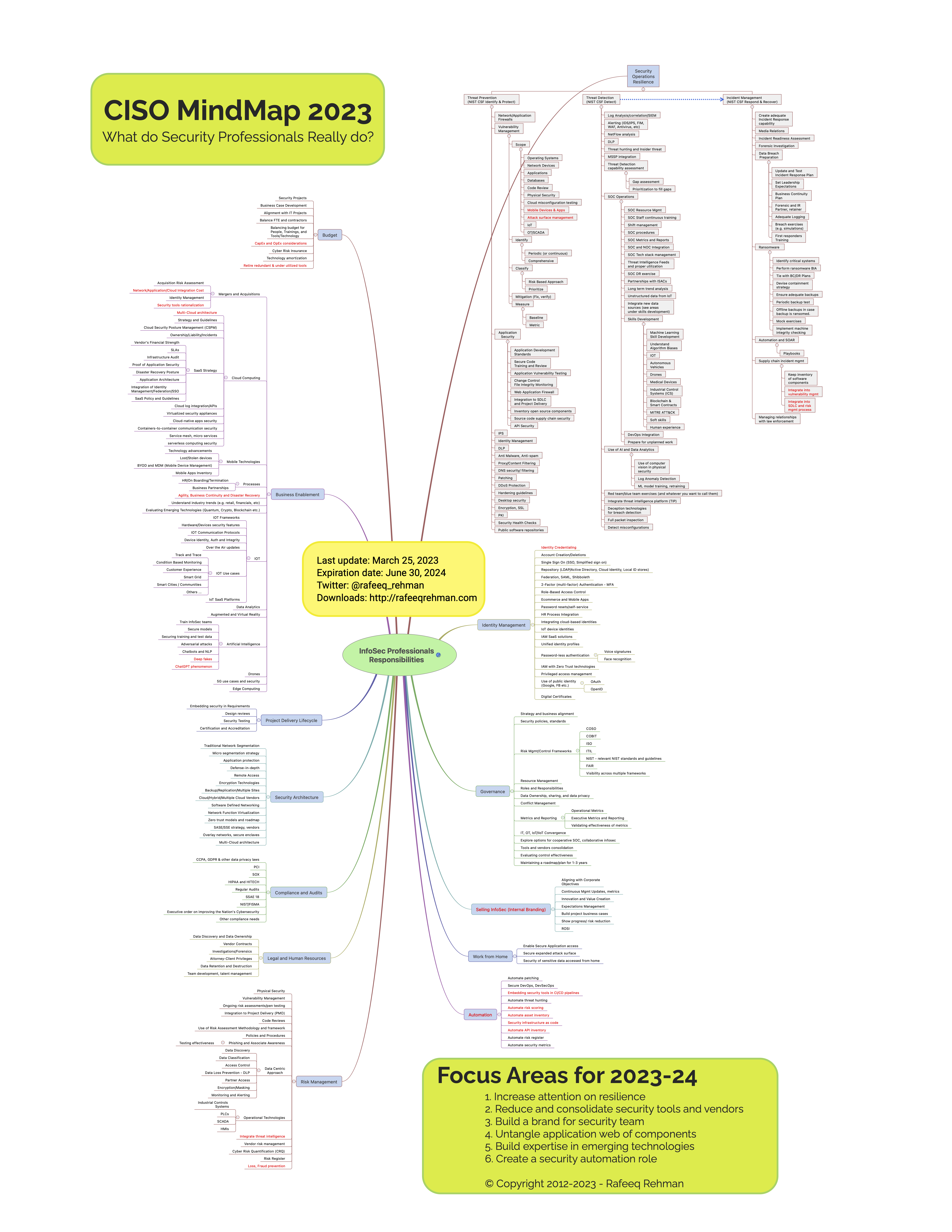
CISO MindMap 2023: What do InfoSec Professionals Really do?Rafeeq Rehman | Cyber | Automation | Digital

The Chief Information Security Officer's Toolkit: Security Program Metrics: Cohen, Fred: 9781878109354: Books - Amazon.ca

CISO-Level Guide: Protecting Your Organization - Cyber Resilience and Financial Organizations - Carnegie Endowment for International Peace